How to use Qiling safe disk
Quick Navigation:
- What is data encryption?
- Why encrypt data?
- What impact will data disclosure have on enterprises / individuals?
- Recommended for you: Qiling safe disk server, it's data encryption tool
- What are the functions of safe disk server?
What is data encryption?
Terms of data encryption include:
Plaintext, that is, original or unencrypted data. It is encrypted by the encryption algorithm, and the input information of the encryption algorithm is plaintext and key; Ciphertext, the format after plaintext encryption, is the output information of the encryption algorithm. The encryption algorithm is public, while the key is not public. The ciphertext shall not be understood by users without key, and shall be used for data storage and transmission; Key is a string composed of numbers, letters or special symbols, which is used to control the process of data encryption and decryption; Encryption, the process of converting plaintext into ciphertext; Encryption algorithm, the transformation method used for encryption; Decryption, the process of transforming the ciphertext inversely to the encryption to obtain the plaintext; Decryption algorithm, the transformation method used for decryption. Encryption technology is a technology to prevent information leakage. Its core technology is cryptography. Cryptography is a subject that studies cryptographic system or communication security. It is divided into cryptography and cryptanalysis; Any encryption system is composed of plaintext, ciphertext, algorithm and key. The sender encrypts the data with the encryption key and sends it out through the encryption device or encryption algorithm. After receiving the ciphertext, the receiver decrypts the ciphertext with the decryption key and restores it to plaintext. In the process of transmission, even if the ciphertext is stolen and obtained by illegal elements, only the unrecognized ciphertext is obtained, which plays the role of data confidentiality.
Why encrypt data?
"Data is the core asset in the information system. The loss, destruction or leakage of data may bring you incalculable losses. Encrypting sensitive data is one of the core means of data security protection. There are two types of data, one is unstructured data, such as documents and pictures, and the other is structured data, such as data in the database. Both forms of data are very important and need to be encrypted Protection. Structured data usually carries very concentrated and valuable information, so it is particularly important to encrypt and protect it.
What impact will data disclosure have on enterprises / individuals?
1. Damage to corporate public reputation
When an enterprise has data leakage, the public will have a sense of mistrust towards the enterprise, which will affect the public's choice. Therefore, the data leakage accident may cause the enterprise to lose a number of customers, including potential customers.After the disclosure of Yahoo email, a large number of users abandoned it, and Yahoo, which is negotiating the acquisition, was even difficult to sell for a time.
2. Damage to the economic interests of enterprises
On the one hand, data itself is a part of enterprise property. When data is leaked, this part of data assets is equivalent to handing over to others, which will threaten the competitiveness of enterprises, indirectly increase costs and reduce benefits.On the other hand, the loss of reputation will lead to the decline of enterprise stock price and the loss of users, which will have a direct impact on the economic interests of enterprises.At the end of last year, when the user data of qudian was leaked, the share price fell continuously, and even fell 30% at the opening.
3. Facing legal charges such as litigation
Once the data is leaked, there will be victims. The victims may be the data source itself, the downstream customers of the enterprise or other partners affected by the data leakageAfter the disclosure of 143 million users of Equifax, a US credit giant, faces a class action lawsuit in the federal court of Portland, with a compensation amount of up to $70 billion.
4. Internal disharmony factors
Some data leaks are caused by hacker attacks, while others are caused by poor internal management. The latter is more likely to make employees distrust the enterprise, and then affect the overall unity of the enterprise.The British supermarket Morrisons, one of the world's top 500 companies, once had a leak accident - the salary details, addresses and bank accounts of 100000 employees were stolen, leaked and sold by internal auditors. Not only the auditors were jailed, but Morrisons was collectively sued by more than 5000 employees, demanding that the enterprise be responsible and compensate for this.
5. Cause high-level shock
There must be various internal problems behind a data leak. When an enterprise has a serious data leak, senior executives usually take responsibility for it or even step down. After the e-mail scandal was exposed, the CEO of Miss America left immediately; After Uber exposed 100000 hacker sealing fees, the chief security officer was dismissed.
Recommended for you: Qiling safe disk server, it's data encryption tool
In what environment can Qiling safe disk server be used?
Windows:win11/win10/win8/win8.1/win7/Vista/xp
Windows server :2019/2016/2012/2008/2003
Operation requirements of safe disk serve.
Disk requirements: more than 1GB free space.
CPU requirements: above 1GHz processor.
Ram: greater than or equal to 1GB.
Hardware supported by safe disk server
Supported hard disks: parallel ATA (IDE / Eide) HDD, serial ATA (SATA / eSATA) HDD, SSD, M2, etc
USB drive: usb1 0 / 2.0 / 3.0, flash drive, etc
Memory card: memory / SD card / CF card / card only, etc
Large capacity slave storage devices: raid / network attached storage (NAS), large capacity hard disk, etc
What crowd can use it?
Small and medium-sized enterprises / technicians / individuals / technical Rookies
What can safe disk server do?
- Personal data encryption
- Enterprise data encryption
- Important file encryption
- Provide three-dimensional protection and all-round concealment of data
- Core technology protects your data
- Good protection effect to enhance the competitiveness of enterprises / individual users
- With high-quality product advantages, I wish your enterprise to take precautions
What are the functions of safe disk server?
Manage virtual disk image files:
1. Create:
Create a suffix of The virtual disk image file of FVD can be configured according to its actual use
- image file: create storage (hard disk) address and file name
- virtual disk size: the default is 8192mb. You can enter data according to your own usage
- sector size: 512 bytes by default. 1024 / 2048 / 4096 data can be selected for filling according to the usage
- format required: when creating an image file, format the disk
- allocate all required disk space immediately
- delete duplicate data in the image: delete duplicate data in the image
- password of image file: image file encryption
- confirm password: confirm the password of the image file again
- create: click the Create button to create the above configuration data
- cancel: return to the main UI
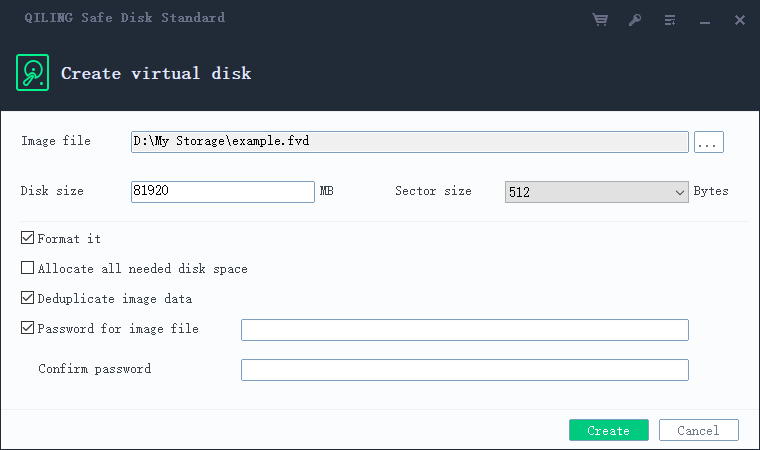
2 mount:
Mount Data settings are made for files with FVD suffix. The figure below shows the function area of mounting image files
- backup point: the time when the virtual disk image was created
- select the attached drive letter: in principle, all drive letters between a and Z can be selected
- password of image file: enter to create The password set when the virtual disk with FVD suffix mirrors the file
- modify password: modify and create The password set when the virtual disk with FVD suffix mirrors the file
- mount as read-only: the files in the mounted drive letter are presented in a read-only manner, and the operation authority is only query
- automatic uninstall when user logs off: automatically uninstall the mounted virtual disk when user shuts down
- automatic backup when uninstalling: when uninstalling the mounted disk, keep the original file + the file with the last target drive letter
- keep the latest backup quantity: keep the latest backup data. You can enter all data within 2 to 32
- mount: verify the data configured in the mount image file list and execute the configured function items
- cancel: return to the main UI
3 unmount
you can operate the uninstall function item for files that already have a mounted drive letter

*NOTE:the operation data corresponding to the secondary function buttons [unmount] / [remove] is the data on the left
4 remove

5 add old image:
add the old image support suffix as fvd/. The data file of ISO is added to the image list

Related Articles
- What is Disk Imaging
- How to Use System Restore in Windows 10
- [New] How to Install and Run 64 Bit Programs on 32 Bit Windows 10/8/7
- Learn How to Make Full Backups with 3 Windows 10 Backup Options
- How to Clone Laptop Hard Drive